Ensure Secure User Access with Deprovisioning
Learn how to effectively manage user access by understanding the best practices for deprovisioning. These tips will help you protect your business from data breaches and cyber attacks.
Are you responsible for ensuring software and network services in your applications remain secure from cyber threats?
If so, you know the importance of adequately managing user access. Implementing a de-provisioning strategy is essential to maintain peak security levels on-premises and protect against data breaches. Deprovisioning is an effective way to grant, modify and revoke user access within your system in real-time and help ensure that only authorized users have access to privileged information.
In this blog post, learn how deprovisioning can be part of a comprehensive security strategy to keep user accounts and devices safe and manage changes in user profiles and permissions quickly and efficiently.
What is deprovisioning, and why is it essential for secure user access
Deprovisioning may sound like a complicated term, but it simply refers to removing access privileges for users who no longer need them.
This is an essential step for maintaining secure user identity and access. It ensures that former employees, contractors, or other individuals with access to privileged information can no longer access it after they've left the organization—failure to have properly deprovisioned former users can leave sensitive data vulnerable to theft or misuse.
That's an example of why organizations must have a straightforward deprovisioning process in place to protect their data and prevent security breaches.
How to implement a successful deprovisioning process in your organization
When it comes to implementing a successful deprovisioning process within your organization, developers should keep several key strategies for deprovision, in mind.
One of the most critical steps is establishing clear guidelines and protocols for removing access to sensitive information and systems. This might involve creating detailed documentation outlining the steps involved in deprovisioning an employee or contractor granted access, and any necessary approvals or authorizations that must be obtained.
Efficient, practical, scalable, and adaptable deprovisioning processes are crucial puzzle pieces for optimal deprovisioning removes your organization. Ensure systems are up to date and meet evolving needs.This might mean integrating automated tools and workflows to streamline the deprovisioning work process or investing in additional training and support for your team to ensure they can execute the strategy seamlessly.
Ultimately, the key to a successful deprovisioning process is to prioritize clear communication, collaboration, and consistency across all teams and stakeholders involved in the manual process.
How to track and monitor user access at all times
For developers, ensuring that user access is tracked and monitored at all times is crucial to maintaining data security and compliance.
By implementing robust monitoring systems that keep track of user activity, developers can identify and prevent potential security breaches before they occur. Some effective methods to accomplish this include implementing audit logging, setting up security alerts that notify administrators of suspicious activity, and requiring multi-factor authentication for sensitive user accounts.
These measures bolster security for new user, and help meet regulatory requirements by providing a detailed record of user activity. With these tools in place, developers can confidently track and monitor user access, knowing that they have taken proactive steps to increase security and ensure the integrity and confidentiality of their systems.
Tips for proper deprovisioning of former employees or contractors
Proper deprovisioning of former employees or contractors is essential to ensure the security of your organization's data and systems.
It's not just enough to hand over the keys and say goodbye. Revoke their access to all company systems, applications hr data, and assets, and plan to remove their credentials immediately. In addition to that, it's also crucial to examine the access they had and the data they were using. Take the necessary steps to ensure that sensitive information is not being mishandled, and immediately bring any irregularities to the attention of relevant authorities.
It's always better to take extra measures when it comes to security, including deprovisioning former employees and contractors.
Common pitfalls to avoid when setting up a deprovisioning system
Setting up a deprovisioning system solution is essential in ensuring data security and compliance. However, there are common pitfalls to avoid to ensure its effectiveness.
One of the most critical mistakes is needing a clear and detailed plan beforehand. With a plan, tracking and managing the scope of the automated user provisioning deprovisioning process becomes more accessible. Another pitfall is failing to conduct regular audits of the automated deprovisioning removes and user provisioning system to identify areas for improvement or potential vulnerabilities.
Additionally, not having an automated system can lead to errors or delays. Finally, not involving key stakeholders, such as HR and IT, can cause miscommunication and ultimately result in an either human error, or an ineffective deprovisioning system.
Avoiding these common pitfalls can help individuals and organizations create a secure and prosperous deprovisioning system.
Best practices for ensuring secure user access with deprovisioning
Ensuring secure user access is a top priority for any organization, and proper deprovisioning is critical to this effort.
Companies can reduce the risk of unauthorized data access or breach by following best practices, such as revoking account, removing user access, immediately upon termination of network services or conducting regular audits of user accounts. It's also essential to have a clear and comprehensive deprovisioning policy outlining the steps necessary to remove user access and safeguard company resources.
In today's fast-paced digital environment, staying on top of security protocols is essential for protecting company and customer data.
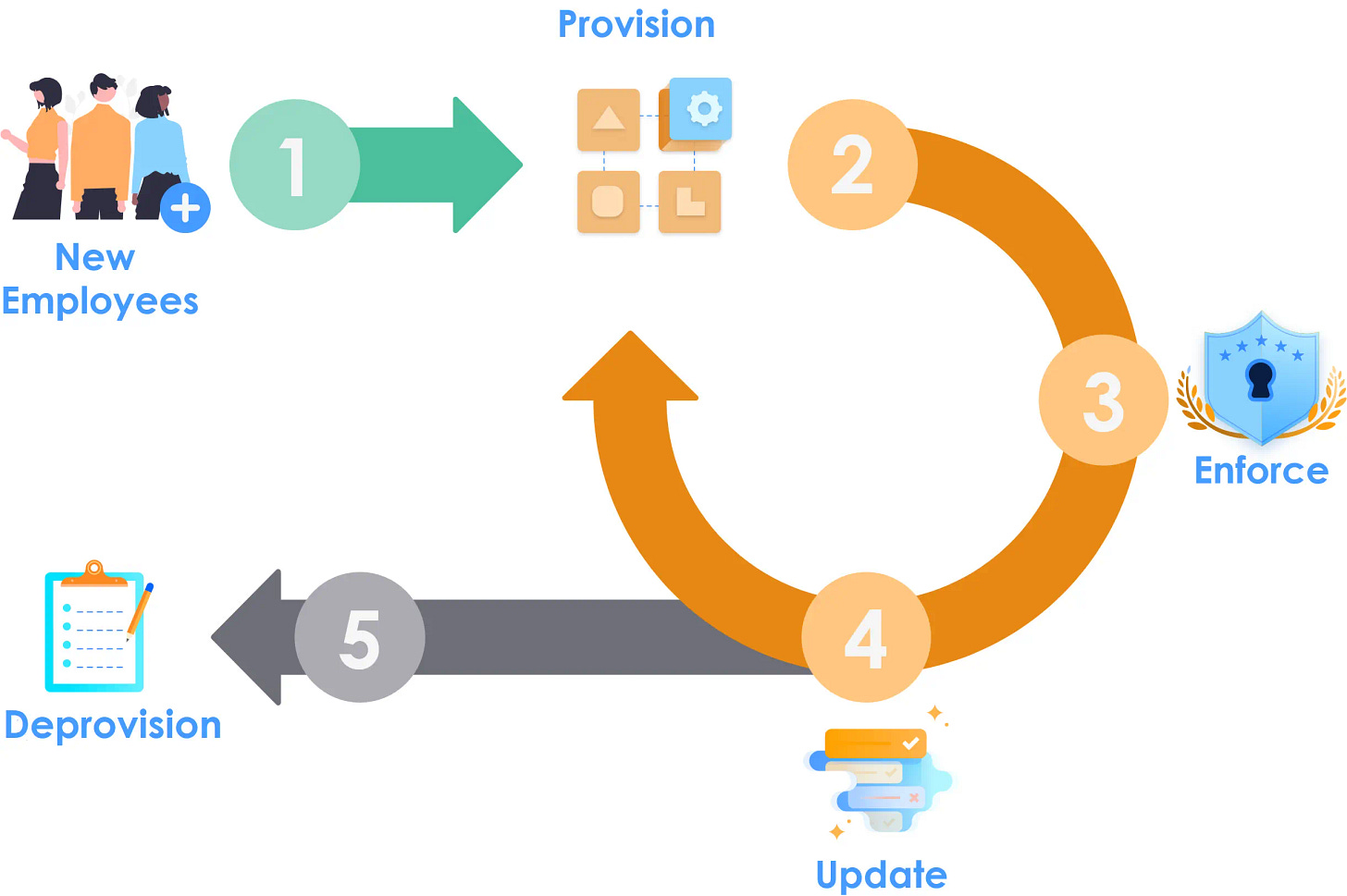
Deprovisioning and provisioning working together
You have already understood precisely why it works. What's an excellent approach to achieving the best results?
Combined with a solid Identity and Access Management Solution enabling to automate user provisioning and deprovisioning within the customer's entire lifecycle management process. Here is some helpful advice on automating user provisioning and deprovisioning works as a critical tenant of Account and access Management solution.
Implement the principle of least privilege (PoLP)
A principle called minimum rights is that a user should only receive access for doing a job.
The decrease in staff resources decreases the effectiveness if an employee leaves the organization. The rules apply for both user provisioning and re-provision. It must affect the employee's role in the provision as the user is entrusted with the tool and applications. It is also helpful for de-provisioning phases, where users move teams and don't need to have access to important information again.
Those who leave the accounts in the company may also have audited accounts at their disposal, accounts that they have yet to be able to use.
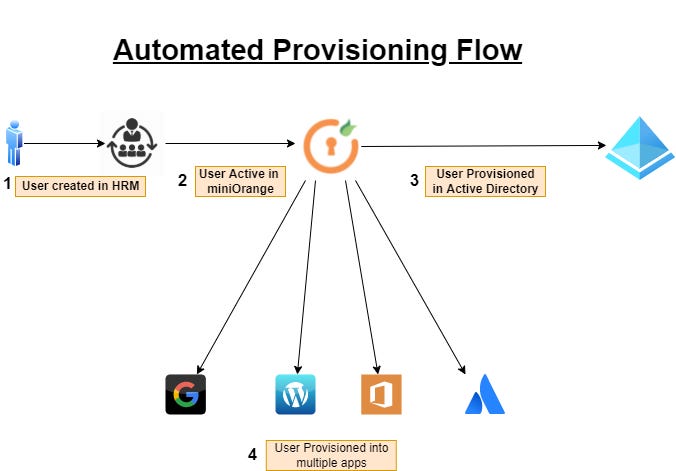
Enable automated provisioning and deprovisioning
Employee access demands develop when a person is promoted to a new position in another company, uses a new device, or adopts a new software tool.
The organizations may restructure or temporarily collaborate with contractors or partner organizations needing limited systems and network operations access. Automation is vital for preventing mistakes when providing information.
This method is also a way for IT managers to save time by preventing human error, errors, and unneeded frustration.
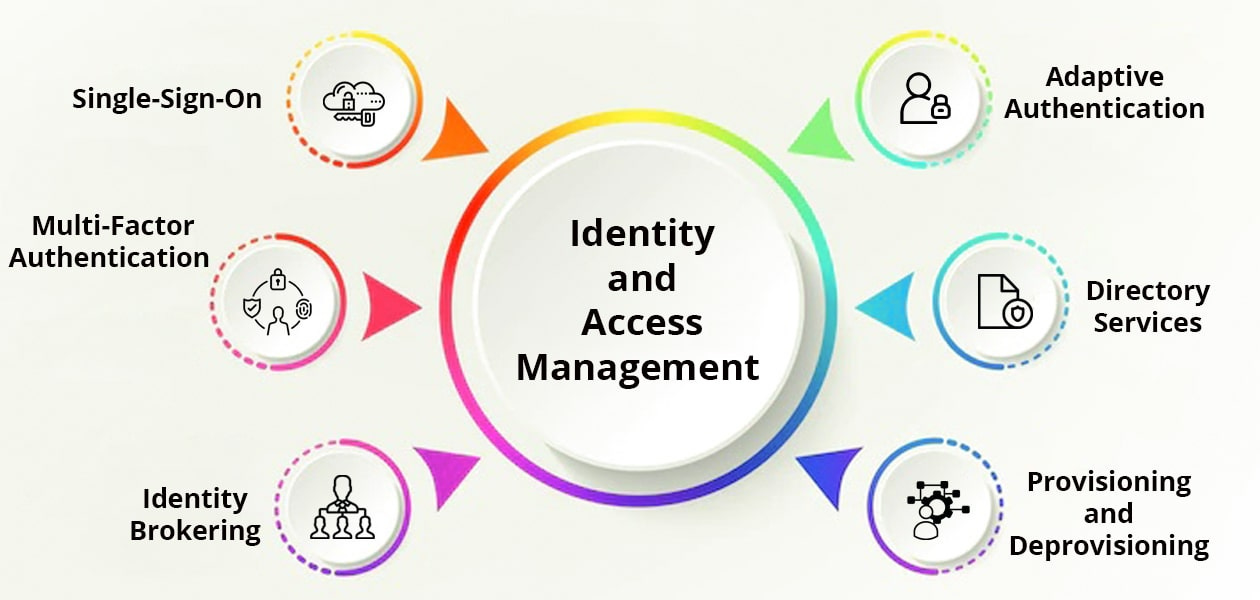
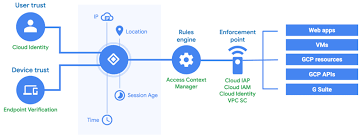
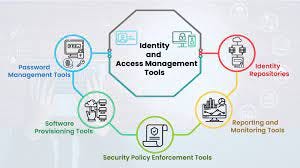
What is an identity and access management (IAM) tool?
Integrated ad networks (AADs), or iAM, is a platform to provide security solutions for businesses that provide the necessary tools to work efficiently in an enterprise environment. It is used to manage user and access rights and identity.
This tool provides companies with the ability to control who has access rights to what systems and data, as well as a way to monitor and log user activity on their networks. With an IAM platform, businesses can ensure that employees have only the information they need when accessing resources or making changes in the system.
It also offers companies a way to detect suspicious activity and respond quickly to minimize any risk of security breaches.
Why user provisioning and deprovisioning matters
In hiring new workers, an organization can create records of their employees.
The employee records will include the following: The next step involves giving employees a free account with the software, services, and tools they need for their jobs. Users provide information in your HR systems, such as adding an employee as a team member, job change, promotions, department transfers, etc.
Best Practices for Secure User Access Control
Ensuring secure user access control is crucial to maintaining the integrity of any system or application.
In today's world, where data breaches and cyber-attacks are rampant, it has become more critical than ever to adopt the best practices for user and access management and control. These measures help keep your data secure and prevent unauthorized access.
One practical approach is to follow the principle of least privilege, which provides users with the minimal level of access necessary to perform their job functions. Additionally, implementing multi-factor authentication and regularly reviewing access permissions can help prevent unauthorized access to sensitive data.
Organizations can minimize risk and protect themselves from potential security breaches by prioritizing secure user access control.
Tips for Establishing a Robust Deprovisioning Strategy
Establishing a robust deprovisioning strategy is crucial to the security and management of any organization.
When an employee departs, it is crucial to instantly revoke their access rights to sensitive information and systems. However, deprovisioning is not a one-time task. It requires careful planning and ongoing monitoring to ensure that former employees cannot gain access to company data after they have left. There are some tips to help establish a solid deprovisioning strategy, including developing a standard exit process, conducting regular reviews of access permissions, and implementing real-time monitoring tools.
By taking these steps, businesses can ensure that former employees do not threaten their cybersecurity or data integrity.
Utilizing advanced tools for secure access control
Maintaining security is a top priority for any organization. Fortunately, with the rise of advanced tools for secure access control, businesses can now protect their sensitive data from unwanted access. These tools allow administrators to control who has access to what data and when all while ensuring that data remains encrypted and secure. Moreover, with the ability to manage access control remotely, your organization can increase efficiency and productivity. The benefits of safe access control are numerous, making it a must-have for any company looking to safeguard its data and assets.
Ensuring compliance with data security regulations
With the ever-growing threat posed by hackers, data security is more important than ever.
Ensuring compliance with data security regulations is critical to protecting sensitive information and preventing unauthorized access. A data breach or in data can have profound consequences that include financial setbacks, harm to reputation and legal penalties. Companies must proactively implement safeguards to prevent data breaches, including encryption, firewalls, and access controls.
As regulations evolve, keeping up-to-date and adapting to new requirements is essential. Companies can protect their customers and businesses from potential harm by prioritizing data security and compliance.
Conclusion
Deprovisioning can significantly improve user access security and reduce the time and cost associated with insecure user access. Organizations can ensure that only authorized personnel can access sensitive information by automating deprovisioning processes, removing user access, and creating access expiration policies. Additionally, the risk of malicious actors gaining unauthorized access to secure systems is reduced through regular reviews of privileged users' activities and data protection tools. As cyber threats grow more complex, organizations should explore how deprovisioning works and automated deprovisioning really works, as a tool to strengthen their security and maintain digital security standards.